Jenkins Slave on AWS EC2 instances with SSH configuration
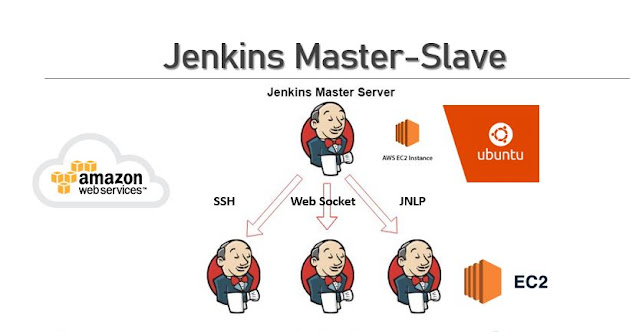
After c onfiguring the Jenkins Maste r we need to configure the slave or agent on EC2 instance. There are various methods to connect with the Slave node. In this post, I would like to share the SSH key-based remoting method. Pre-requisites Jenkins Master already Up and Running Java (JDK) installed on the Slave node Here we are in the slave machine and proceed with the following steps for configure a SSH based Jenkins slave. How to create user and generate ssh-key on Slave? Login to slave node terminal using ssh or PuTTY switch to root user. useradd jenkins_slave mkdir -p /home/jenkins_slave usermod -d /home/jenkins_slave jenkins_slave tail -1 /etc/passwd # To check useradded to userlist Now switch to the newly created user 'jenkins_slave'. sudo su - jenkins_slave SSH Key generate for 'jenkins_slave' user with the following command: cd .ssh ssh-keygen -t rsa -N "" The above command will create two files in /home/jenkins_slave/.ssh folder id_rsa (p...
