Kubernetes Security - Multiple Cluster with Multiple User Config
Hello Guys! in this post we are going to explore about the Kubeconfig. This is a special configuration that will be part of Kubernetes Security. We can configure multiple clusters and different users can access these Kubernetes cluster. We can also configure the users can have access to multiple clusters.
When we started working on Kubernetes Cluster there is a config file automatically generated for us.
To access a Kube Cluster using the certificate files generated for admin user can be given as follows:kubectl get pods \ --server controlplane:6443 --clisent-key: admin.key --client-certificate admin.crt --certificate-authority ca.crtEvery time passing all these TLS details(server,client-key,client-certificate, certificate-authority) including in the kubectl command is tedious process. Instead of this we can move TLS Certificate file set into a config file that is called kubeconfig file. The usage will be as follows
kubectl get pods --kubeconfig configUsually this config file will be stored under .kube inside the home directory. If the config file present in this $HOME/.kube/ location and file name as config is automatically detected by the kubectl command while executing.
What is KubeConfig contains?
Cluster section used to define the multiple sets of Kubernetes clusters such as development, testing, preprod and prod environment wise cluster or different organizations integrations use separate clsuter or different cloud providers can have clusters example google-cluster or azure-cluster etc.
And in the Users section we can have admin user, developer user etc. These users may have different privileges on different cluster resources.
Finally contexts manages the above two sections together mapping to form a context. here we will get to know that which user account will be used to access which cluster.
Remember, we are not going to create any new users or configuring any kind of user or authorization in this kubeconfig. We will be using only the existing users with their existing privileges and defining what user acces what cluster mapping. This way we don't have to specify tht user certifcates and server URL in each and every kubectl command to run.
The kubeconfig is in yaml format which basically have above mentioned three sections. |
| Kubernetes Configuration with different clusters map to Users |
apiVersion: v1
kind: Config
clusters:
- name: vybhava-prod-cluster
cluster:
certificate-authority: /etc/kubernetes/pki/ca.crt
server: https://controlplane:6443
- name: vybhava-dev-cluster
cluster:
certificate-authority: /etc/kubernetes/pki/ca.crt
server: https://controlplane:6443
- name: vybhava-gcp-cluster
cluster:
certificate-authority: /etc/kubernetes/pki/ca.crt
server: https://controlplane:6443
- name: vybhava-qa-cluster
cluster:
certificate-authority: /etc/kubernetes/pki/ca.crt
server: https://controlplane:6443
contexts:
- name: operations
context:
cluster: vybhava-prod-cluster
user: kube-admin
- name: test-user@vybhava-dev-cluster
context:
cluster: vybhava-dev-cluster
user: test-user
- name: gcp-user@vybhava-gcp-cluster
context:
cluster: vybhava-gcp-cluster
user: gcp-user
- name: test-user@vybhava-prod-cluster
context:
cluster: vybhava-prod-cluster
user: test-user
- name: research
context:
cluster: vybhava-qa-cluster
user: dev-user
users:
- name: kube-admin
user:
client-certificate: /etc/kubernetes/pki/users/kube-admin/kube-admin.crt
client-key: /etc/kubernetes/pki/users/kube-admin/kube-admin.key
- name: test-user
user:
client-certificate: /etc/kubernetes/pki/users/test-user/test-user.crt
client-key: /etc/kubernetes/pki/users/test-user/test-user.key
- name: dev-user
user:
client-certificate: /etc/kubernetes/pki/users/dev-user/dev-user.crt
client-key: /etc/kubernetes/pki/users/dev-user/dev-user.key
- name: gcp-user
user:
client-certificate: /etc/kubernetes/pki/users/gcp-user/gcp-user.crt
client-key: /etc/kubernetes/pki/users/gcp-user/gcp-user.key
current-context: operations
To view the configuration of current cluster you must have the config in $HOME/.kube/config
The content of kubernetes configuration can be view with the following command: :kubectl config view
 |
| Kubernetes Cluster view when default config used |
kubectl config view --kubeconfig=vybhava-config
Know your Kubernetes cluster
To check the list of cluster(s) exist in the default kubernetes cluster configkubectl config get-clustersWork with your customized config file vybhava-config to know clusters list
kubectl config get-clusters --kubeconfig=vybhava-config
 |
| Knowing about Kubernetes cluster from Kube Config |
KuberConfig user details
To check the list of user(s) exist in the default kubernetes cluster configkubectl config get-usersWork with your customized config file vybhava-config to know user list
kubectl config get-users --kubeconfig=vybhava-config
 |
| KubeConfig getting the users list |
KubeConfig Context
Here the context will be using users, clusters and each context is identified with a name define also here we can sees at the end of the configuration current context.
To find how many contexts in vybhava-config To know for default cluster contexts :kubectl config get-contextsTo identify what user configured in the 'operator' context we need to use the 'get-contexts' option the mapping output is displayed as a table where 'CURRENT' context will be pointed with '*' in the column.
kubectl config --kubeconfig=vybhava-config get-contexts
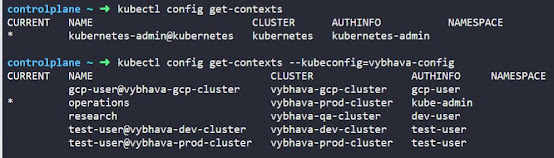 |
| Kubernetes Config getting Contexts using kubectl |
Here in the Context section we could add a field namespace that can be specific to project module such as production cluster can be mapped to HR application that runs with hr-finance,hr-hirings namespce.
Here we have executed all possible choices for fetching the Users, Clusters, Context from KubeConfig object. Now let's try to set the context
delete user
kubectl config --kubeconfig=vybhava-config get-users kubectl config --kubeconfig=vybhava-config delete-user test-user kubectl config --kubeconfig=vybhava-config get-users
 |
| Deletion of Users from Config |
delete cluster
kubectl config --kubeconfig=vybhava-config get-clusters kubectl config --kubeconfig=vybhava-config delete-cluster vybhava-gcp-cluster kubectl config --kubeconfig=vybhava-config get-clusters
 |
| Kubernetes Cluster deletion from KubeConfig |
delete context
kubectl config --kubeconfig=vybhava-config get-contexts kubectl config --kubeconfig=vybhava-config delete-context gcp-user@vybhava-gcp-cluster kubectl config --kubeconfig=vybhava-config get-contexts
 |
| Deletion of Context from Kube Config |



Comments