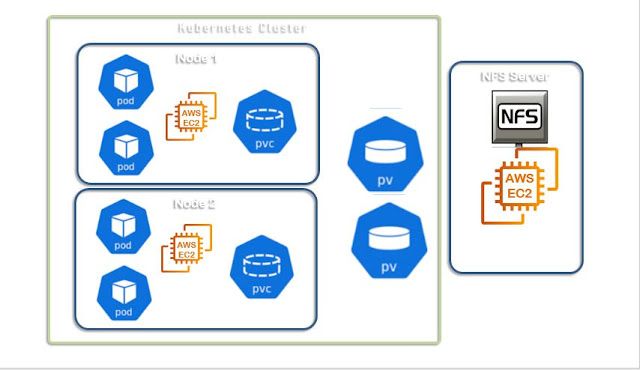
Microk8s Installation on Ubuntu and Configure Kubernetes Dashboard

Microk8s is the most happening thing in Kubernetes World. Here I would like to share my exploration of microk8s. Earlier there was 'Minikube' which is targets to Developers community to reduce the operations. Assumption You know how to create a VM using Vagrant, VirtualBox that we had discussed in the other blogposts already so here I'm skipping it. Microk8s installation on Ubuntu To install you should be super user on your Ubuntu VM sudo -i The snap is a package manager available in all Linux distributions. Here in the Ubuntu 18.04 validating is it available. Check snap package tool available snap version Now we all set, run the install the microk8s command here the --classic is must snap install microk8s --classic --edge Check the version microk8s.kubectl version --short Create an alias to simplify your command alias k="microk8s.kubectl" Let's use k now k get nodes k get nodes -o wide # check the namespaces list k get namespaces k get a...